How do you monitor your Salesforce.com logins?
For enterprises currently using the Salesforce.com or
Force.com platform, you understand that Salesforce.com offers many
layers of security that protect your data and limit access to your
data. However most corporate security breaches are not due to
technical loopholes in software and architecture, they are due to
human vulnerabilities. For example, a hacker tricks someone
into revealing their username and password and then they login
remotely, undetected. Today’s popular Intrusion Detection and
Prevention Software only works at the network and host level and do
not include login location analysis. We
provide login location information with mapping, rules and
alerts to prevent fraudulent logins.
Intrusion Detection with Login Locator for Salesforce.com
As a Systems Administrator or Information Security Officer,
how do you know where your users are logging in from? Are you
alerted if they login from a foreign country or from two locations
geographically distant from each other? Do you currently
monitor or take action on failed login attempts?
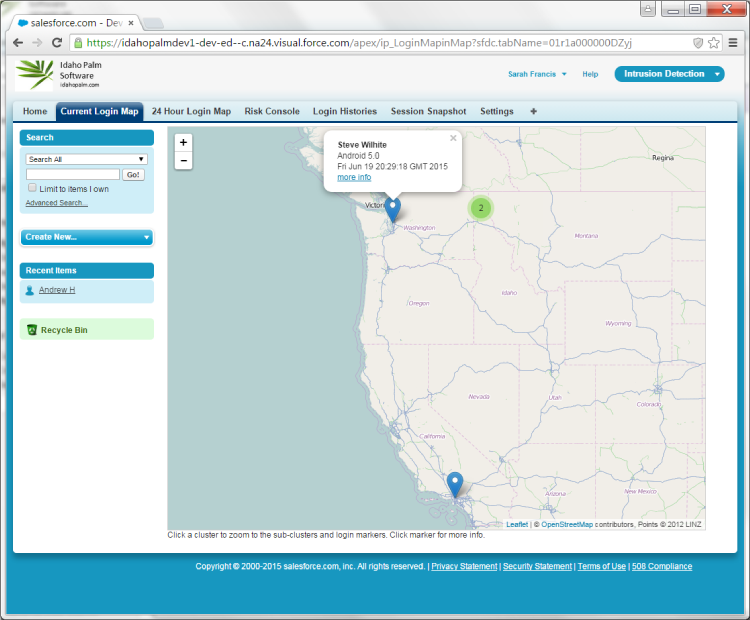
Idaho Palm Software offers Intrusion Detection with Login
Locator(IDLL) in the Salesforce.com AppExchange to combat this
vulnerability. IDLL takes information from the Salesforce.com
platform’s login history table and obtains IP location information to provide administrators
an actual location for each login.
Now Available
Free
Trial / Purchase
Demo Video
Did you Know?
Fortune Magazine
Most companies believe they'll be hacked in 2015, poll shows
A common refrain among security professionals goes like this.
There are two kinds of companies in the world: those that know
they’ve been hacked, and those that have been hacked and don’t yet
know it. More.
CNBC
Top 5 cybersecurity risks for 2015
From identity theft and fraud to corporate hacking attacks,
cybersecurity has never been more important for businesses,
organizations and governments.
More.